Cyber-security: A necessary component of railway businesses in the digital age
Posted: 21 February 2018 | Sharvind Appiah (EEIG ERTMS Users Group) | No comments yet
The railway industry is experiencing a critical phase in its existence. They face numerous challenges and changes which they must overcome to ensure they remain reliable and sustainable in the future. Some of the issues that need urgent attention include increasing competition from other modes of transport, the massive costs of maintaining railway operations and the cyber-security challenges surrounding digitalisation, discusses Sharvind Appiah, Lead Engineer of Cyber-security from the EEIG ERTMS Users Group…


Cyber-security challenges
Railways have traditionally been a highly mechanical, engineering-intensive business – hence there is a massive gap to bridge into an environment which is highly dependent on technology. Obsolete technologies and techniques such as circuit-switching, GSM-R and complete embedded systems are a hindrance to the evolution of the railway business. It is becoming increasingly obvious that actors in the railway ecosystem must urgently adopt more modern techniques such as packet-switching networks, component-based systems and open architecture practices.
There are essentially three key elements to be considered: The change of technology, the system’s lifecycle and the associated costs. There is no option but to shift from proprietary technology to as many off-the-shelf components as possible. This will help the railway systems become more adaptable and allow for a more rapid adoption of technology advances, consequently impacting the difference in system lifecycles between that of control and IT systems. The inability of railway systems to evolve as rapidly as their underlying technology penalises the whole industry and this must be addressed. Finally, the cost element is a critical factor in the equation – the more obsolete a technology is, the more expensive it becomes to sustain due to the increasing scarcity of components, which impacts the economies of scale, or lack thereof.
The downside of equipping the railways for the modern age is the associated threats that accompany the adoption of new technology – threats that have thus far eluded them. The threat landscape and the attack surface of railways are naturally increasing as the boundaries between the various actors and different sections of railway businesses are becoming increasingly integrated.
However, cyber-security challenges do not only cover technical attacks and threats such as malware and viruses, there is far more to cyber-security management than this form of protection. There are also issues surrounding governance, risk management, security operations and compliance monitoring activities that require attention in order to maintain a reasonable maturity level of cyber-security in railway companies.
Roles and responsibilities
There are several actors in the railway business within which there are several subdivisions that must share the responsibility of cyber-security for the whole industry. These responsibilities will naturally differ depending on the individual actors. Figure 1 below represents an example – and not the complete scope – of the responsibilities of the various actors.
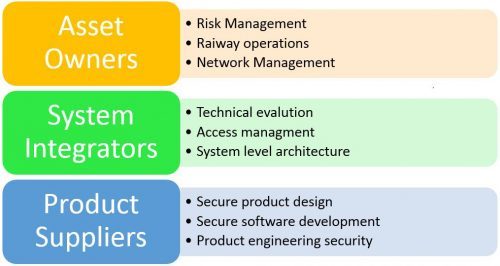

Figure 1
This segregation of cyber-security responsibilities not only differs between actors but can also be taken on by a single actor. If we take, for example, the typical role of an infrastructure manager, we can easily identify three traditional silos:
- The Command & Control Systems (CCS) environment, which is mainly related to railways signalling and safety systems
- The rail traffic and operations environment, which has the core responsibility of managing the traffic (Traffic Management Systems – TMS) and scheduling activities of train traffic
- The Corporate business, which mainly addresses customer related information, information displays systems and ticketing systems, among others.
There is a cultural and traditional way of conducting business that has evolved over recent decades and has culminated in these three silos operating independently. However, the cyber-security challenges facing the industry today require these three functions to coordinate their cyber-security activities and implement complementary measures to effectively address the threats of today, as well as the future. This not only requires combatting technical challenges but also overcoming the cultural challenge for railway businesses to manage cyber-security as efficiently as possible.
It is important to be aware of the global concepts around governance and the risk-related activities around cyber-security management, and not be blinkered by individual roles and responsibilities.
Cyber-security governance
There are several principles that businesses are required to take into consideration when managing cyber-security internally. It is essential to have mature governance principles that align cyber-security with the business in order to assure the success of any cyber-security initiative.
More and more businesses are doing this and for the railways it is a real opportunity to address cyber-security at the highest possible level within the organisation. Top level management is ultimately accountable for cyber-security in the organisation; they have the prime responsibility for ensuring that the company assets and information are adequately safeguarded. They can delegate the responsibility to one or several other entities to implement the cyber-security countermeasures, but they will always be responsible for validating cyber-security investments and resourcing requirements for the management of cyber-security in their organisations.
The next step is to implement a strategy that is appropriate to the business, the operations and the assets within its scope. This means that different business areas (assets owners, system integrators and product suppliers) would have to focus on different aspects of cyber-security and would require adequate resources (financial and non-financial) to implement these measures. There needs to be a clear indication of the priorities of the organisation and the objectives of the cyber-security programme to be implemented – the strategic alignment between business goals and cyber-security is essential to the success of a cyber-security initiative.
Cyber-security operations
The cyber-security operations cover all the activities that are undertaken end-to-end to implement and maintain cyber-security activities. The starting point is what cyber-security practitioners call the ‘risk-based approach’. To be able to justify the specific activities and investments in cyber-security, the motivation behind it must be assessed. If we look at the fundamentals of cyber-security – which is to safeguard the business assets of an organisation and protect against threats – the only way to justify an investment is to evaluate the level of risk to which the organisation is exposed and identify what level of risk is acceptable. This classic risk management activity is already used in other industries, such as finance and insurance, and adopting this kind of risk-based approach to the railway industry would be a decisive first step towards cyber-security maturity.
Other complementary activities, such as asset management, network management, access control, patch management, vulnerability management, standards and regulatory compliance, become easier to address when organisations have clear indications and supporting evidence regarding the efforts required to implement these activities to a level that is adapted to their specific organisation. We must bare in mind the ubiquitous reality that resources are not unlimited and therefore be very strategic in our approach to implementing cyber-security management. Another important concept to remember – especially with an organisation where numerous departments have the same security concerns – in order to maximise the efficiency of cyber-security activities, organisations should avoid duplications and re-inventing the wheel. Fostering stronger collaboration and coordinated actions in cyber-security will help an organisation increase the efficiency of their countermeasures and optimise their resources and investments.
Cyber-security lifecycle
Heraclitus said: “The only constant in life is change” and this perfectly applies to cyber-security. The systems and environment under its scope are constantly changing, as characterised by new systems being implemented, new suppliers and service providers being contracted or just a different solution being adopted in the business. Therefore, cyber-security needs to adapt to these perpetual changes and evolutions. Cyber-security is implemented as a lifecycle that includes risk assessments, countermeasure implementations and evaluations of the cyber-security maturity level achieved. Essentially, organisations must understand that managing cyber-security is not a project that requires implementation by a definite date, but more a continual process that requires execution and updating on a regular basis, or when a subsequent change occurs in the system.
Conclusion
Cyber-security becomes a necessary component of railway businesses as the industry adopts new technologies. The digital railway projects across Europe, and the need to integrate with other modes of transport, require the railway community to open their boundaries to other actors in multi-modal transportation solutions. The new regulations around cyber-security, such as the Directive on Security of Network and Information Systems (the NIS Directive) and the General Data Protection Regulation (GDPR), require railway companies to comply as much as possible with their standards and undertake certain obligations. Cyber-security is a highly technical and operational topic, yet it still needs to be driven by top level management. They have to make sure that adequate measures are implemented and that the necessary resources are made available to effectively deploy a cyber-security programme in their organisation.